之前开发者都收到了苹果2017年的新开发者审核协议更新通知
2017年3月8
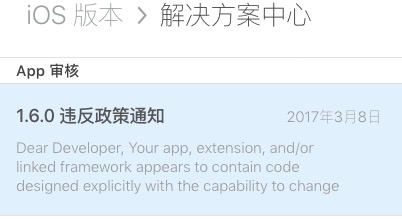
注意..是女神节这天。大量开发者收到了被拒绝 被警告的邮件,内容如下:
Dear Developer,
Your app, extension, and/or linked framework appears to contain code designed explicitly with the capability to change your app’s behavior or functionality after App Review approval, which is not in compliance with section 3.3.2 of the Apple Developer Program License Agreement and App Store Review Guideline 2.5.2. This code, combined with a remote resource, can facilitate significant changes to your app’s behavior compared to when it was initially reviewed for the App Store. While you may not be using this functionality currently, it has the potential to load private frameworks, private methods, and enable future feature changes.
This includes any code which passes arbitrary parameters to dynamic methods such as dlopen(), dlsym(), respondsToSelector:, performSelector:, method_exchangeImplementations(), and running remote scripts in order to change app behavior or call SPI, based on the contents of the downloaded script. Even if the remote resource is not intentionally malicious, it could easily be hijacked via a Man In The Middle (MiTM) attack, which can pose a serious security vulnerability to users of your app.
Please perform an in-depth review of your app and remove any code, frameworks, or SDKs that fall in line with the functionality described above before submitting the next update for your app for review.
Best regards,
App Store Review
苹果审核协议中有这样一节:
Apple Developer Program License Agreement
3.3.2 An Application may not download or install executable code. Interpreted code may only be
used in an Application if all scripts, code and interpreters are packaged in the Application and not
downloaded. The only exception to the foregoing is scripts and code downloaded and run by Apple's builtin WebKit framework, provided that such scripts and code do not change the primary purpose of the Application by providing features or functionality that are inconsistent with the intended and advertised purpose of the Application as submitted to the App Store.App Store Review Guideline
2.5.2 Apps should be self-contained in their bundles, and may not read or write data outside the designated container area, nor may they download, install, or execute code, including other iOS, watchOS, macOS, or tvOS apps.
随后JSPatch群里 ,github上都炸了锅 : https://github.com/bang590/JSPatch/issues/746
react-native 的情况 :https://github.com/facebook/react-native/issues/12778
Weex ::https://github.com/alibaba/weex/issues/2875
JSPatch的作者bang也收到了邮件:
2017年6月1
如果还含有热更新功能的应用,在6月12日将会遭到苹果的下架。这也许是苹果给的最后期限。
6 月 1 日,部分开发者在 itunesconnect 后台收到了一则通知:苹果要求当前含有热更新功能的 App,在 6 月 12 日前移除相关代码,否则这些 App 可能会下架。
Dear Developer,
In March of this year we notified you that your app contains code designed explicitly with the capability to change your app’s behavior or functionality after App Store Review approval, which is not in compliance with section 3.3.2 of the Apple Developer Program License Agreement and App Store Review Guideline 2.5.2. We requested that you remove any code, frameworks, or SDKs that fall in line with the functionality described above before submitting the next update for your app for review.
As of this message, we have not received a compliant update for your app.
To ensure there is no interruption of the availability of your app, please submit an update by June 12th, 2017. If we do not receive an update by that date, your app may be removed from the App Store.
If you have any questions about this information, please reply to this message to let us know.
Best regards,
App Store Review
6 月 12日前后,App Store 的 App 下架数量很可能会出现一次高峰。
提醒大家,关注自家 itunesconnect 后台有没有收到相关通知
还是尽快老老实实的更新未含有热更新的新程序包,以免影响使用。
为什么突然爆发
突然爆发并非偶然,苹果的审核指南一直明确,禁止下载可执行代码,虽然JSPatch等库使用了JavaScriptCore来巧妙的实现,但也不是长久之计,很多开发者不自觉的使用其来下发私有方法等等行为迟早会被苹果发现。也极大的威胁到了极其注重安全的苹果
再有就是一切涉及到网络的都会有安全的风险
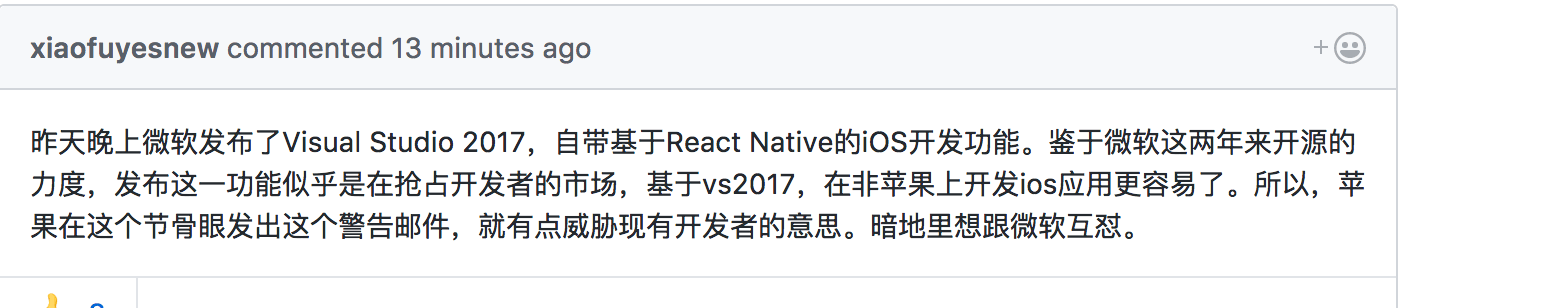
还有一个有意思的事实,昨天VS2017发布,号称内置iOS模拟器,直接开发React Native:
所以很多人也得出了一个灾难性结论"苹果封杀混合开发",JSPatch等热更新是误伤....
总结下波及到的库
rollout,react native,weex,JSPatch,bugtags,个推 ,bugly with hotfix
查看是否使用热更新
最直接当然是查看有没有JSPatch等热更新的库。
但是很多第三方也内部集成了JSPatch,这时只能用终端脚本find一下了
|
1 |
grep -r JSPatch . |
当然有些人把JSPatch库完全重命名了,如果第三方SDK改名后使用并且出现提示排查起来略有点困难
为什么没使用热更新会收到邮件
个人认为苹果是批量扫描runtime JSPatch等关键词并且群发的,苹果没办法批量检测remote script(远程脚本下载)
所以机智的检测热更新可能使用到的runtime方法,比如method_exchangeImplementations。这样基本全覆盖了那些使用热更新的APP。
警告"下载脚本代码且使用runtime方法实现的的APP"下一个版本改掉,如果不改。有可能被下架被拒绝上架。
JSPatch是"下载脚本代码且使用runtime",并不是针对JSPatch一个库
rollout,react native,weex都会有这种提示。
bugtags ,个推 这种看似没有热更新的其实内部集成了JSPatch等库,也会有这种提示
Runtime不能继续用了?
个人认为原生代码中使用runtime还是没问题,只是为了提醒那些使用了runtime并且下载远程脚本改变app行为的人。
如果苹果把runtime变成私有方法或去掉.那么Objective-C的优势大大的没有了.....
怎么解决?
如果是类JSPatch这种只用来热更新的,暂时去掉这些热更新的库。
JSPatch更新了最新版,进行了强制加密,据说很多人上架成功了.可以试试
但是前提是要检查其他第三方sdk是否包含了JSPatch,更新到第三方库到最新版本.
如果是类React Native,抓紧转行吧。。哈哈哈(我开玩笑的。。。)
转载请注明:天狐博客 » Apple向热更新下达最后通牒